Features:
1. Scheduler
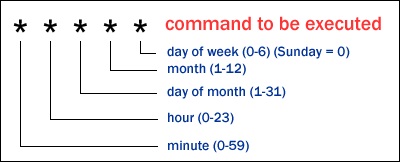
2. Rules (Cron entries) are based on times:
a. minute (0-59)
b. hour (0-23)
c. day of the month (1-31)
d. month (1-12)
e. day of the week (Sun,Mon,Tue, etc. OR 0-7)
f. command to execute (shell, perl, php, etc.)
3. Wakes up every minute in search of programs to execute
4. Reads cron entries from multiple files
5. Maintains per-user and system-wide (/etc/crontab) schedules
/etc:
cron.d/
cron.deny - denies cron execution by user
cron.monthly/ - runs jobs monthly
cron.weekly/ - runs jobs weekly
cron.daily/ - runs jobs daily
cron.hourly/ - runs jobs hourly
crontab - contains system-wide schedules
Note: '*' wildcard in a time column means to run for all values
Per-user Crontabs:
Stored in: /var/spool/cron
Task:
1. Create a cron entry for the user 'student1'
a. su student1
b. crontab -e
c. create an entry, minus the name of the user
Note: 'crontab -l' - enumerates per-user cron entries
System-wide Crontab:
Stored in: /etc/crontab
Task:
1. Create a cron entry in: /etc/crontab
Note: 'crontab -l -u username' - enumerates per-user cron entries
Thanking you
Hope U Like it.....