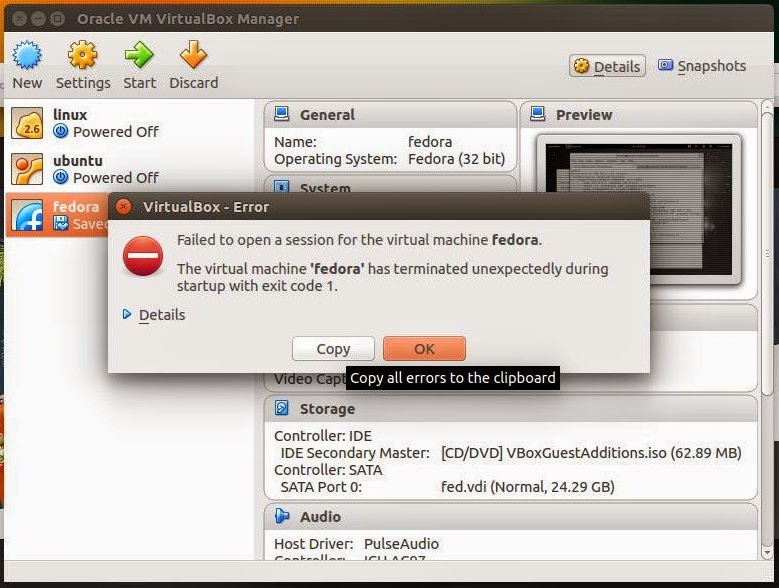
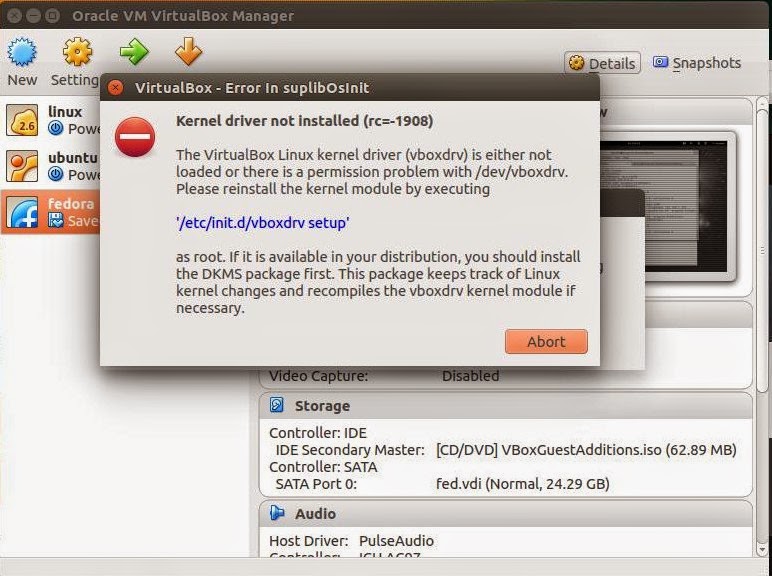
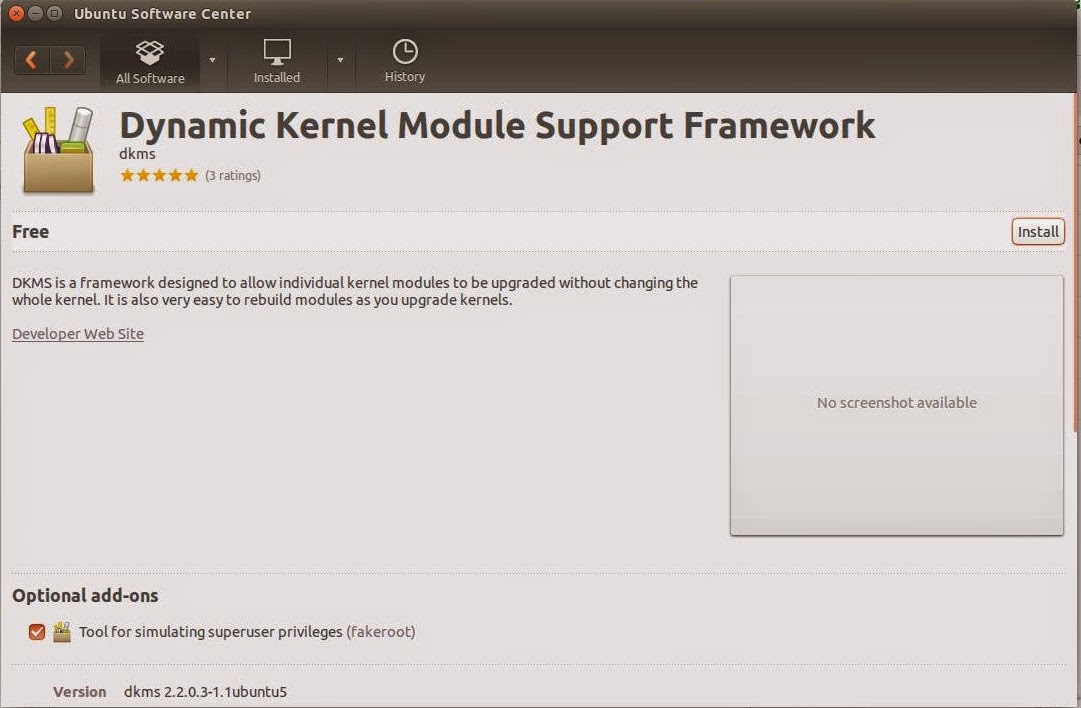
What is xargs ?
xargs is a very powerful command that takes output of a command and pass it as argument of another command. Following are some practical examples on how to use xargs effectively.
Xargs Example 1:-
# find ~ -name *.log -print0 | xargs -0 rm -f
Xargs Example 2:-
Get a list of all the *.conf file under /etc/. There are different ways to get the same result. Following example is only to demonstrate the use of xargs. The output of the find command in this example is passed to the ls l one by one using xargs.
# find /etc -name "*.conf" | xargs ls l
Xargs Example 3:-
If you have a file with list of URLs that you would like to download, you can use xargs as shown below.
# cat url-list.txt | xargs wget c
Xargs Example 4:-
Find out all the jpg images and archive it.
# find / -name *.jpg -type f -print | xargs tar -cvzf images.tar.gz
Xargs Example 5:-
Copy all the images to an external hard-drive.
# ls *.jpg | xargs -n1 -i cp {} /external-hard-drive/directory
Thanking You
Hope U Like it........